
Security and Legality
Registering and playing for real money is legal as the company operates under Curacao eGaming license #8048/JAZ2018-040.

1Win is an in-demand bookmaker website with a casino among Indian players, offering a variety of sports disciplines and online games. Delve into the exciting and promising world of gambling and get 500% on four first deposit bonuses up to 170,000 INR and other generous promotions from 1Win.
GET +500% ON FIRST DEPOSIT
Copy and use promo code to get bonus


Spaceman

Pinata Wins

Fortune Mouse

Hot Fiesta

Big Bass Crash

Fortune Dragon
1Win has been in the industry for over 10 years, establishing itself as a reliable betting option for Indian players.
The site operates under an international license, ensuring compliance with strict regulatory standards. It has gained recognition through numerous positive user reviews. Its operations are fully legal, adhering to gambling laws in every jurisdiction where it is available.
1Win promotes responsible gambling and provides dedicated resources on this topic. Players can access various tools, including self-exclusion, to manage their betting activities responsibly.

 Company
Company
|
| MFI Investments Ltd |
 Year
Year
|
| 2016 |
 Languages
Languages
|
| English, Hindi, +17 |
 Available Categories
Available Categories
|
| Sports Betting, Slots, Table Games, Live Casino, and others. |
 Providers
Providers
|
| Evolution Gaming, Pragmatic Play, Spribe, Ezugi, Play’nGO, BGAMING, Microgaming, NetEnt, and +120 |
 Welcome Bonus
Welcome Bonus
|
| 500% on four first deposits up to 170,000 INR. |
 Payment Methods
Payment Methods
|
| Net Banking, UPI, Paytm, Skrill, Neteller, Cryptocurrency, and so on. |
 Customer Support
Customer Support
|
| 24/7 Live Chat, Email Support, FAQ |
 Mobile Compatibility
Mobile Compatibility
|
| iOS, Android (Mobile App available) |
 Licensing
Licensing
|
| Curacao, № 8048/JAZ 2018-040 |
 Responsible Gaming
Responsible Gaming
|
| Self-Exclusion, Deposit Limits, Responsible Gaming Tools |
 Security
Security
|
| SSL Encryption, Secure Payment Processing |
 Social Media
Social Media
|
| Facebook, Instagram, Twitter |
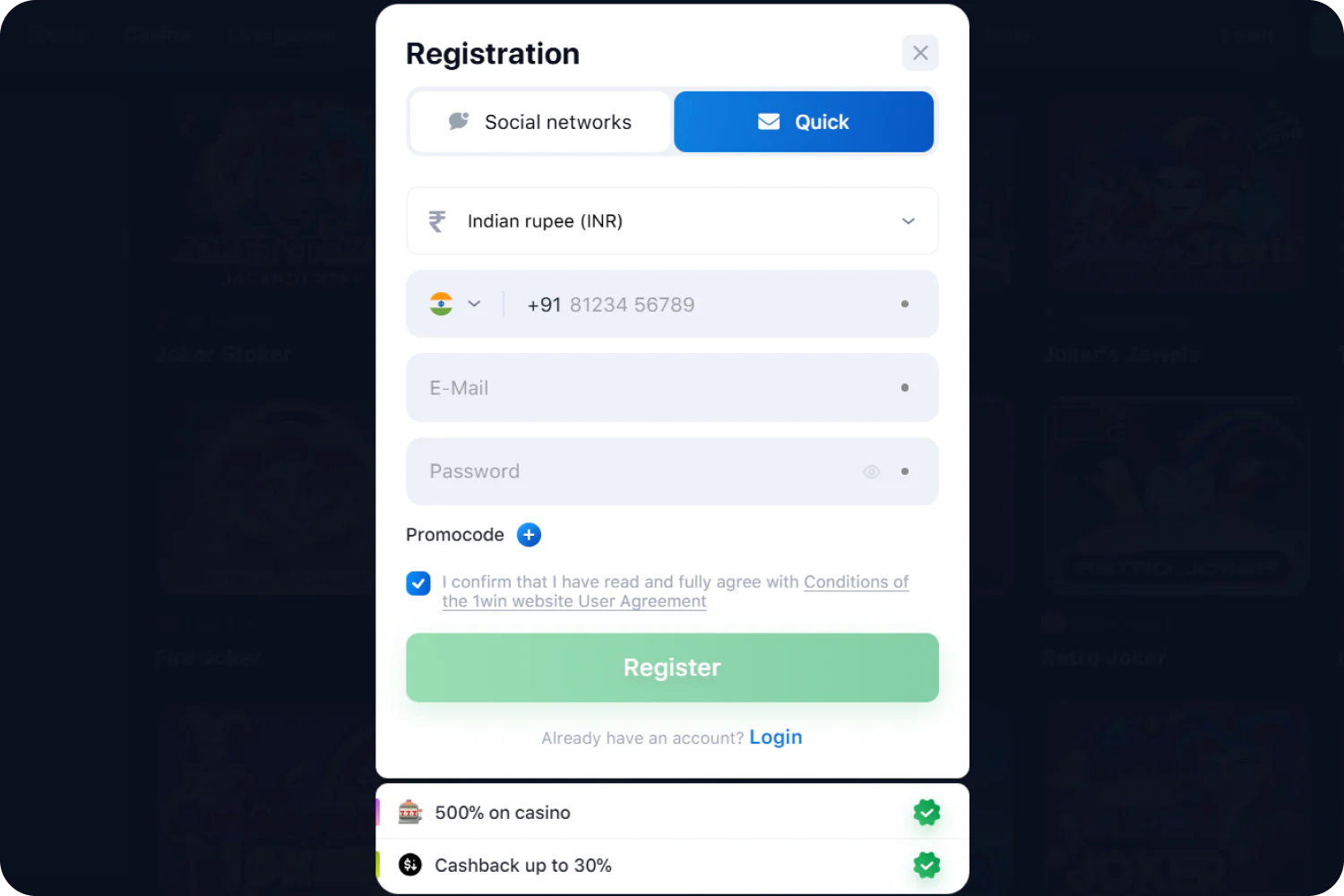
To join, players must register on 1win. Below is a guide for players on how to create a new account:
Once you already have a personal account, you can login to 1Win from any device. How to do this is described below:

1win offers a lucrative promotional program for new and regular players from India. The site offers promotions for online casino as well as sports betting. All bonus offers have time limits, as well as participation and wagering conditions.



1Win welcomes new bettors with a generous welcome bonus pack of 500% in total. Registered users may claim the reward when complying with requirements. The foremost demand is to deposit after registration and get an immediate crediting of funds into their main account and a bonus percent into the bonus account.

The 30% cashback from 1win is a refund on your weekly losses on Slots games. The cashback is non-wagering and can be used to play again or withdrawn from your account. Cashback is awarded every Saturday based on the following criteria.
| Cashback | Amount of Bets per Week (INR) | Maximum Cashback Amount (INR) |
| 1% | from 100,000 | 3,000 |
| 2% | from 300,000 | 4,000 |
| 3% | from 500,000 | 5,000 |
| 4% | from 800,000 | 8,000 |
| 5% | from 1,000,000 | 15,000 |
| 10% | from 10,000,000 | 20,000 |
| 20% | from 20,000,000 | 30,000 |
| 30% | from 50,000,000 | 50,000 |
Cricket is undeniably the most popular sport for 1Win bettors in India. To help bettors make wise choices, the bookmaker also offers the most recent data, live match updates, and professional analysis. Cricket betting provides countless options for excitement and rewards, whether it’s picking the winner of a high-stakes event or guessing the match’s top scorer.

The 1Win betting site provides you with a range of possibilities if you’re interested in cricket. You may bet on the side you believe will win the game as a standard match wager, or you can wager more precisely on which batter will score the most runs throughout the match.
In addition, the bookmaker provides various cricket betting alternatives including total runs scored in the match, runs scored in a particular over, and wickets that will fall within a given time frame. Here is the list of available cricket competitions on 1Win:

1Win India betting options are not limited to cricket. Bettors may follow and place their bets on numerous other sports events that are available in the sports tab of the site. Here are those in demand.

Football, or soccer as it is known in certain places, is a popular sport across the world. Various outcomes, such as both sides scoring, the result at halftime, and player performance indicators, are available for wagering. Among all the tournaments you can find:

Every day the bookmaker offers more than 100 tennis matches. It doesn’t matter if you are new to the sport or a longtime fan, because you can always research statistics to compare players’ results and try to make a winning bet. Among the prestigious tennis tournaments you can find on 1win:

Basketball is another sport at 1WIn on which Indian punters can bet on team results, point totals and player performances. Bets are available on the following events:

If you are not very interested in sporting events, but actively follow cyber sports, 1win has something to offer you. Betting on esports has more than 10 disciplines, among which you can find Dota 2, CS 2, Valorant, and others. You can bet on team wins or individual player points. Find out which cybersports events are present in the 1win:

The procedure of placing a bet on 1win is quite simple. You can do it in just a couple of minutes, use the guide below:

The bookmaker at 1Win provides a wide range of betting options to satisfy gamblers from India, particularly for well-known events. The most popular types and their characteristics are shown below.
This kind of bet is simple and focuses on picking which side will win against the other or, if appropriate, if there will be a draw. It is accessible in all athletic disciplines, including team and individual sports.
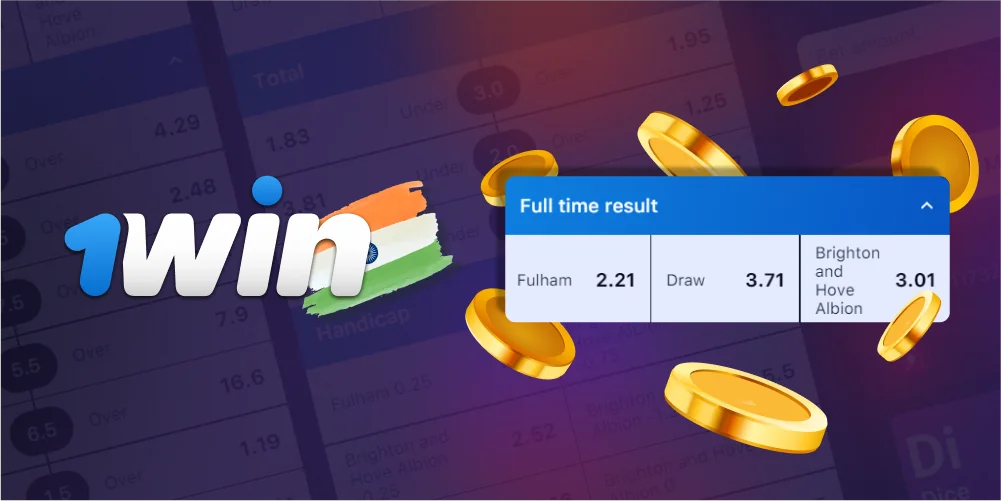
Total bets, sometimes referred to as Over/Under bets, are wagers on the presence or absence of particular performance metrics in the results of matches. For example, there are bets on the total number of football goals scored or the total number of rounds in a boxing match.
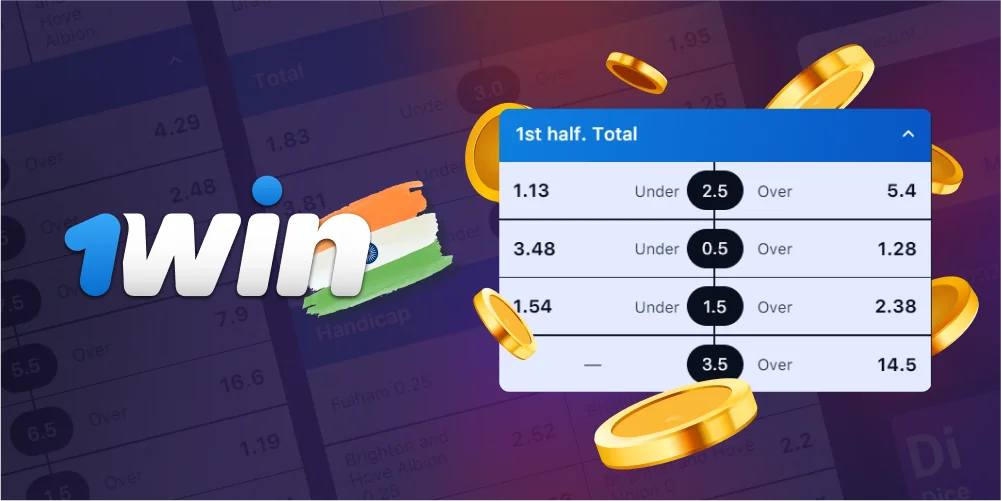
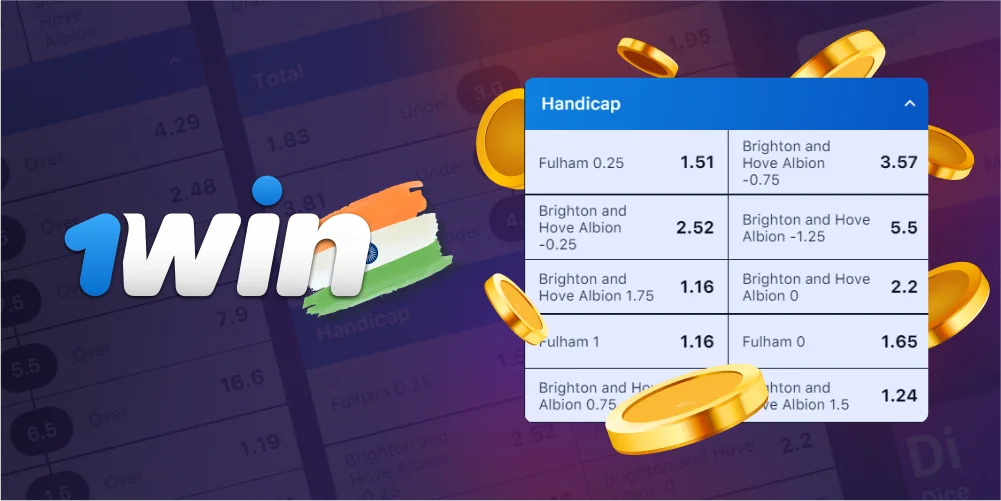
With handicap betting, one team is given a virtual advantage or disadvantage before the game, creating an even playing field. This kind of bet involves guessing how much one side will do better than the other at the end of the game. It can be either positive or negative.
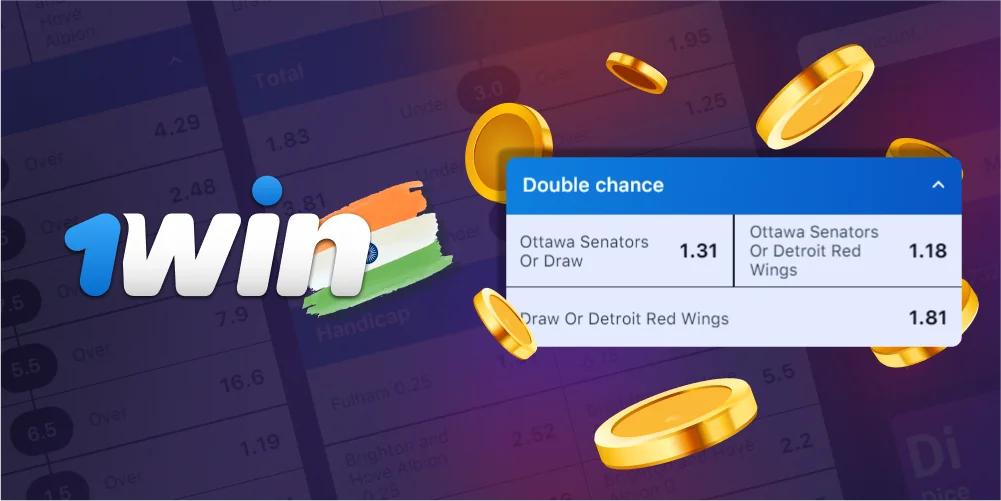
By using Double Chance, bettors can place bets on two probable outcomes of a match at the same time, lowering their chance of losing. But because there is a higher chance of winning with Double Chance bets than with Match Outcome bets, the odds are usually lower.
1Win Players in India frequently make a few basic mistakes when selecting a wager, which might decrease their chances of winning. Here are a few of these errors to stay away from:

The collection of 1win casino games is simply amazing in abundance and variety. Players can find more than 12,000 games from a wide variety of gaming software providers, of which there are more than 170 on the site. Find out more about the most important categories below.

This is the largest category on 1Win. There are over 10,545 games from fruit classics to branded video slots. The following slots are the most popular slots among Indian players:

Poker, roulette, blackjack, and the like can be found among all table games on 1win casino. More than 700 variants of games in this category are ready to provide you with an exciting gaming experience. The most in-demand games in this category are:

There are over 500 online games available in the live dealer lobby. The most popular live dealer games on 1Win are:

Being a software developer, 1Win provides players with a unique chance to try the games that are available only at this casino. Below is a list of 1Win’s own games:

| Game | Player | Rate | Multiplier | Winning |
|---|---|---|---|---|
 Brew Brothers |
Winggft6 |
2,950 INR |
x 3.02 |
8,909 INR |
 Chicken Rush |
Rajj76ggG |
1,600 INR |
x 2.67 |
4,272 INR |
 Merge Up |
Playeefrr6 |
3,100 INR |
x 3.98 |
12,338 INR |
 SpaceXY |
Surrlq1212 |
2,300 INR |
x 4.01 |
9,223 INR |
 Le Pharaoh |
Alexookl0 |
2,200 INR |
x 2.14 |
4,708 INR |
 Burning Chilli X |
kayyu99oi |
2,400 INR |
x 4.51 |
10,824 INR |
 Aviator |
AooilLLo22 |
1,900 INR |
x 2.98 |
5,662 INR |
 Need for X |
1249961HRj |
2,300 INR |
x 2.65 |
6,095 INR |
 Duel at Dawn |
Harry6688U |
2,100 INR |
x 1.98 |
4,158 INR |
 StarX |
Lckiihjj8 |
3,200 INR |
x 3.81 |
12,192 INR |
With 1Win app, bettors from India can take part in gambling and bet on sports at any time. If you have an Android or iPhone device, you can download the mobile app completely free of charge. This software has all the features of the desktop version, making it very handy to use on the go.

A single safe source of download app is the 1win mobile site. Download the apk for Android in a few clicks:
You can also download the 1win mobile app for iPhone or iPad from the official website:
Players from India can easily fund their betting accounts and 1Win will not charge additional transaction fees. In the table below you will find the available payment methods:
| Payment System Name | Minimum deposit amount, INR | Fees | Transaction processing time |
|---|---|---|---|
|
|
300 | 0% | Instant |
|
|
300 | 0% | Instant |
|
|
300 | 0% | Instant |
|
|
300 | 0% | Instant |
|
|
1,000 | 0% | Instant |
|
|
390 | 0% | Instant |
|
|
300 | 0% | Instant |
|
|
300 | 0% | Instant |
|
|
300 | 0% | Instant |
|
|
300 | 0% | Instant |
|
|
300 | 0% | Instant |
|
|
0.00016312 BTC | 0% | Instant |
1Win is known as a reliable bookmaker. By choosing this site, users can be sure that all their personal data will be protected and all winnings will be paid out instantly. Below are advantages of betting company over other bookmakers:

Registering and playing for real money is legal as the company operates under Curacao eGaming license #8048/JAZ2018-040.

You can make deposits from INR 300 and withdraw winnings with no fees from INR 950.

New players are offered a welcome package, while regular players are offered gifts in the Free Money section and tournaments with large prize pools.

You can bet on Sports, eSports and Virtual Sports as well as Trading, Fantasy Sport and Twain Sport.
There are many positive reviews about the 1Win bookmaker. Users share their excellent gambling experience and emphasize such aspects as the uniqueness and variety of games, a rich database of world-known providers, amicable support, instant transactions, high RTP, and many more.

The most important thing for me is a fast payout, and to my great surprise, 1win is paying out my winnings, and fast enough. In all the time I’ve played, I’ve never had to contact the support team, everything is so automated that I have no idea who it was made for in the first place. Quick payouts, quick verification, easy deposits. Everything is cool!
I’ve been playing on the 1Win for about half a year now. I think they have a very cool design. I’ve played on many sites, but I’ve settled on 1win because they know exactly what they’re doing. What’s more, I really like the support service. With many bookmakers you have to wait all the time and go through a lot of bureaucracy while 1win is all about people.
I have been betting on 1Win since last year, the top sporting events have good odds, the usual ones not so much. I do not have any problems with payments, delays are very rare, in fact all the money is paid.
1win has not let me down yet, the site is working stably, money is withdrawn in the minimum time. It is convenient to bet on sports, the calculation of winnings is always correct. I would like to diversify the list of bets, but in general you can play.
User data is protected through the site’s use of advanced data encryption standards. Furthermore, 1Win uses strong security measures to protect players’ personal information and money in addition to taking a proactive approach against fraud, money laundering, and other unlawful actions.

Through the betting website’s support service, you can easily report any technical difficulties and get answers to any of your questions. The support team may be contacted in the following ways:
Depending on the approach used, the processing time may change. Credit card and electronic wallet payments are frequently processed instantaneously. Bank transfers might take longer, often ranging from a few hours to several working days, depending on the intermediaries involved and any extra procedures.
Gamblers can choose to control their money and establish betting restrictions. This feature encourages prudent money management and gaming.
There are 27 languages supported at the 1Win official site including Hindi, English, German, French, and others.
1Win uses state-of-the-art encryption technology to safeguard user information. This involves protecting all financial and personal data from illegal access in order to give gamers a safe and secure gaming environment.
The live streaming function is available for all live games on 1Win. It implies that users may track the gameplay in real-time. With interactive buttons and menus, the player has complete control over the gameplay. Every game’s presenter communicates with participants via the screen.
Last updated:
Add a comment